VPNs for Vendor Access
In an era where cybersecurity is threatened by increasingly sophisticated attacks, it is crucial to protect critical infrastructure without compromising operational efficiency. At Zaphire, we believe VPNs have no place in a modern security architecture.
This article explains why, and how our zero-trust approach provides safer, more precise, and fully traceable access without opening the door to unwanted traffic.
At Zaphire, protecting your building infrastructure from cybersecurity threats is central to our mission. Every aspect of our platform is engineered to ensure security, visibility, and control - without limiting operational flexibility. We apply a modern, zero-trust philosophy to all connections, meaning every user, device, and session is authenticated, authorized, and continuously verified.
Why Zaphire Will Never Introduce VPNs
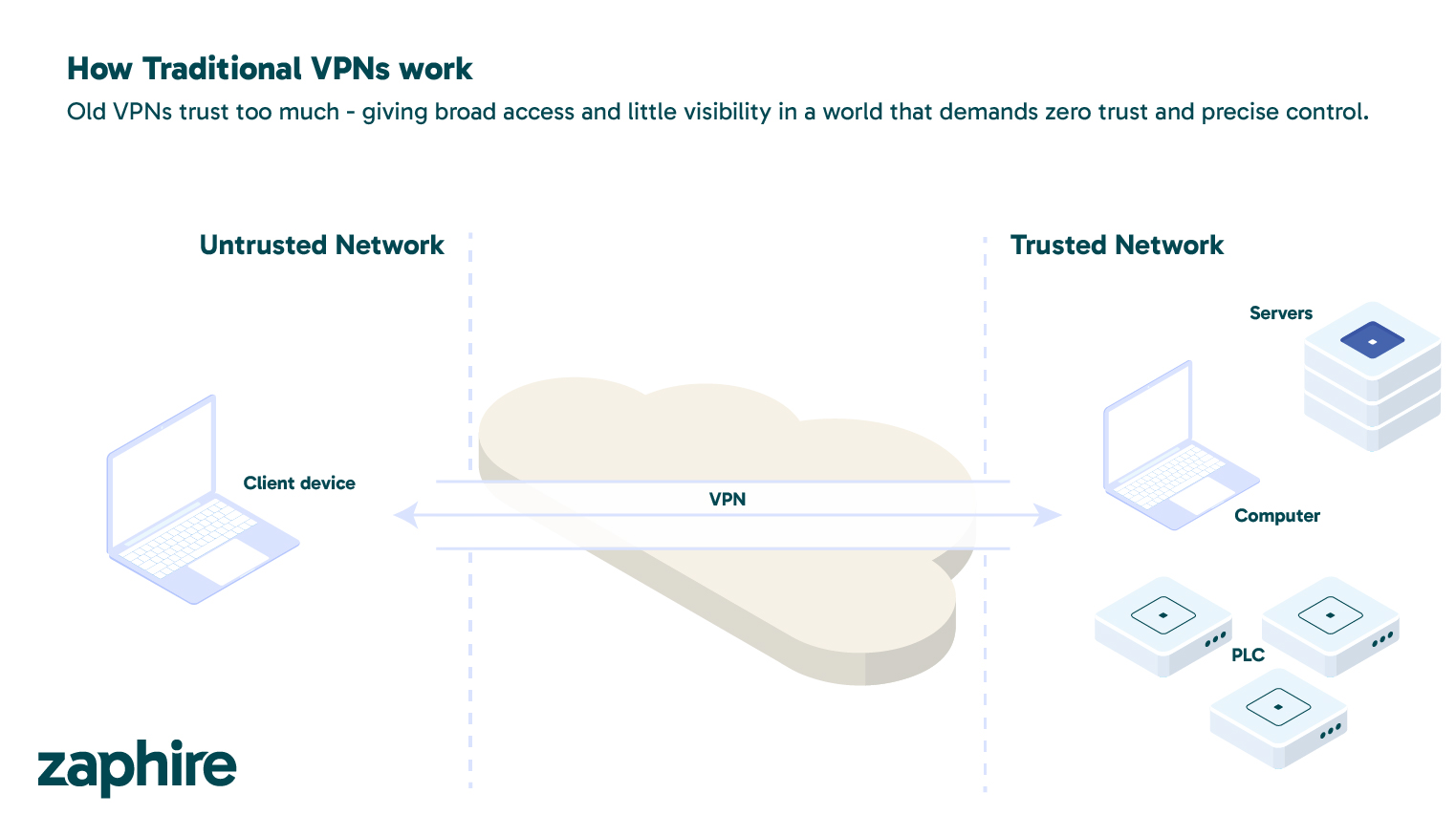
This commitment is why Zaphire will never introduce a VPN into your network through our platform. While VPNs were once seen as a reliable tool for remote connectivity, they expose organizations to significant risk. A VPN can grant broad access to internal networks, which means a single compromised device can become an entry point for attackers or ransomware. In environments controlling critical infrastructure, that risk is unacceptable.
We believe in access that is controlled, auditable, and context-aware, not blind trust once connected. This approach is based on the same principles described in our article on Zero Trust networking in building automation.
Remote Access the Right Way
We understand that technicians and engineers may need remote access to PLCs or control devices for programming and troubleshooting. However, Zaphire believes that facilitating such deep network access should be handled by the building’s IT department, not through our platform. This ensures compliance with organizational security policies and preserves network integrity.
Our responsibility is to keep your building’s systems secure and reliable, not to bypass cybersecurity defenses. Secure access is also a prerequisite for efficient operation and energy optimization in modern buildings.
If you are new to building automation, you can read more about what a Building Management System (BMS) is and how it connects technical systems.
Why VPNs Don’t Fit Modern Security Standards
Traditional VPNs were designed for an era of perimeter-based networks, where once you were inside, everything was trusted. That model doesn’t work in today’s distributed, cloud-connected, and automation-driven environments. VPNs typically provide users with access to large parts of the network, creating opportunities for lateral movement if an account or device is compromised.
Even when protected by multi-factor authentication, VPNs rely on outdated assumptions of trust and often lack granular visibility. Security teams may not be able to see what users do once connected, and VPN traffic is frequently treated as ‘safe,’ delaying detection when a breach occurs.
In short, VPNs assume trust by location. Modern security assumes trust must be earned and verified continuously.
Zaphire’s Approach: Secure WebSocket and HTTPS Connections
Zaphire takes a completely different approach. We use secure WebSocket and HTTPS connections-application-layer protocols that provide end-to-end encryption, fine-grained access control, and complete session transparency.
Our use of WebSockets allows persistent, encrypted communication between authorized systems and services without ever exposing the broader network. Each connection is scoped to a specific endpoint or API, ensuring that even if a user’s device were compromised, it could not move laterally or access unrelated systems.
This architecture follows the same zero-trust principles used in modern building automation platforms.
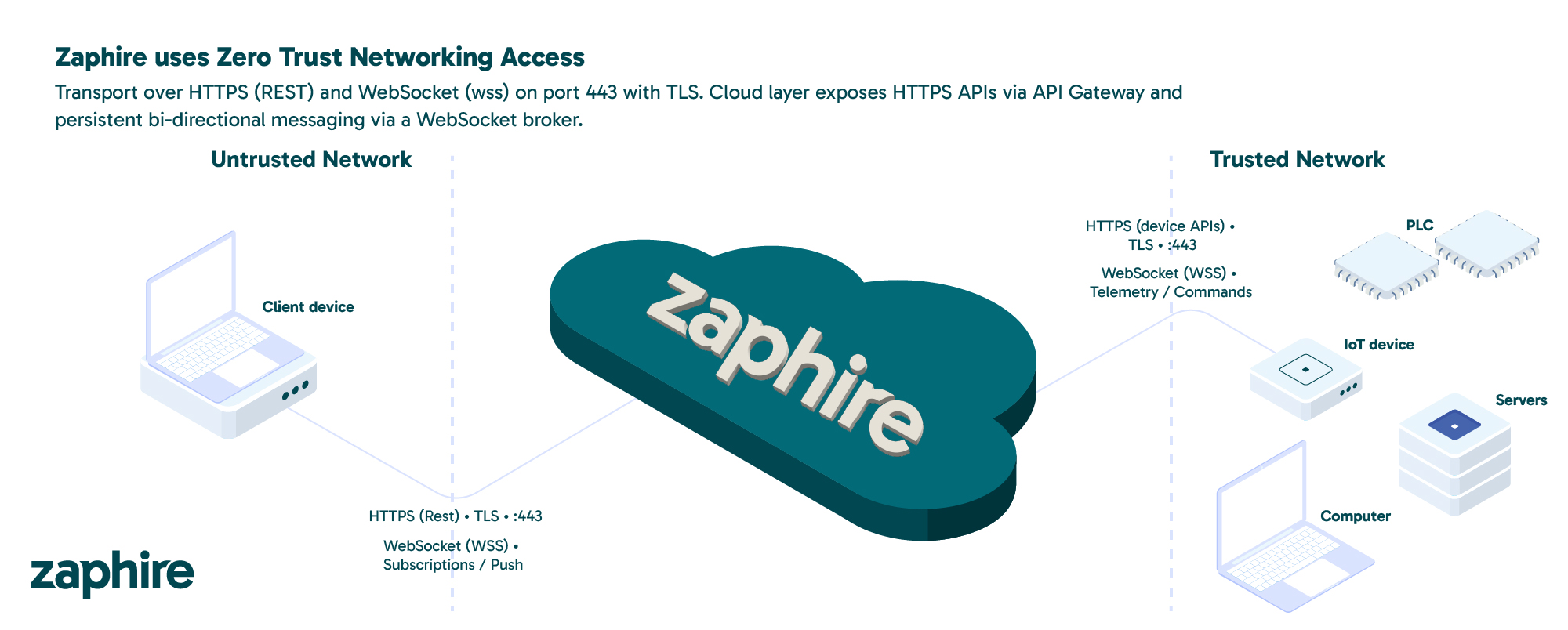
All communications through our platform are encrypted with TLS and secured using modern authentication methods such as OAuth2 and mutual TLS. This ensures that only verified users and approved devices can interact with our systems, and only for as long as they are authorized to do so. This design eliminates the need for network-level tunnels altogether, replacing them with tightly controlled, transparent application sessions.
For building operators and IT teams, Zaphire’s model means faster onboarding of vendors, full visibility into every connection, and no need to open inbound firewall ports. Remote work stays secure, without adding network complexity or maintenance overhead.
A Real-World Example: How Ransomware Spreads Through VPNs
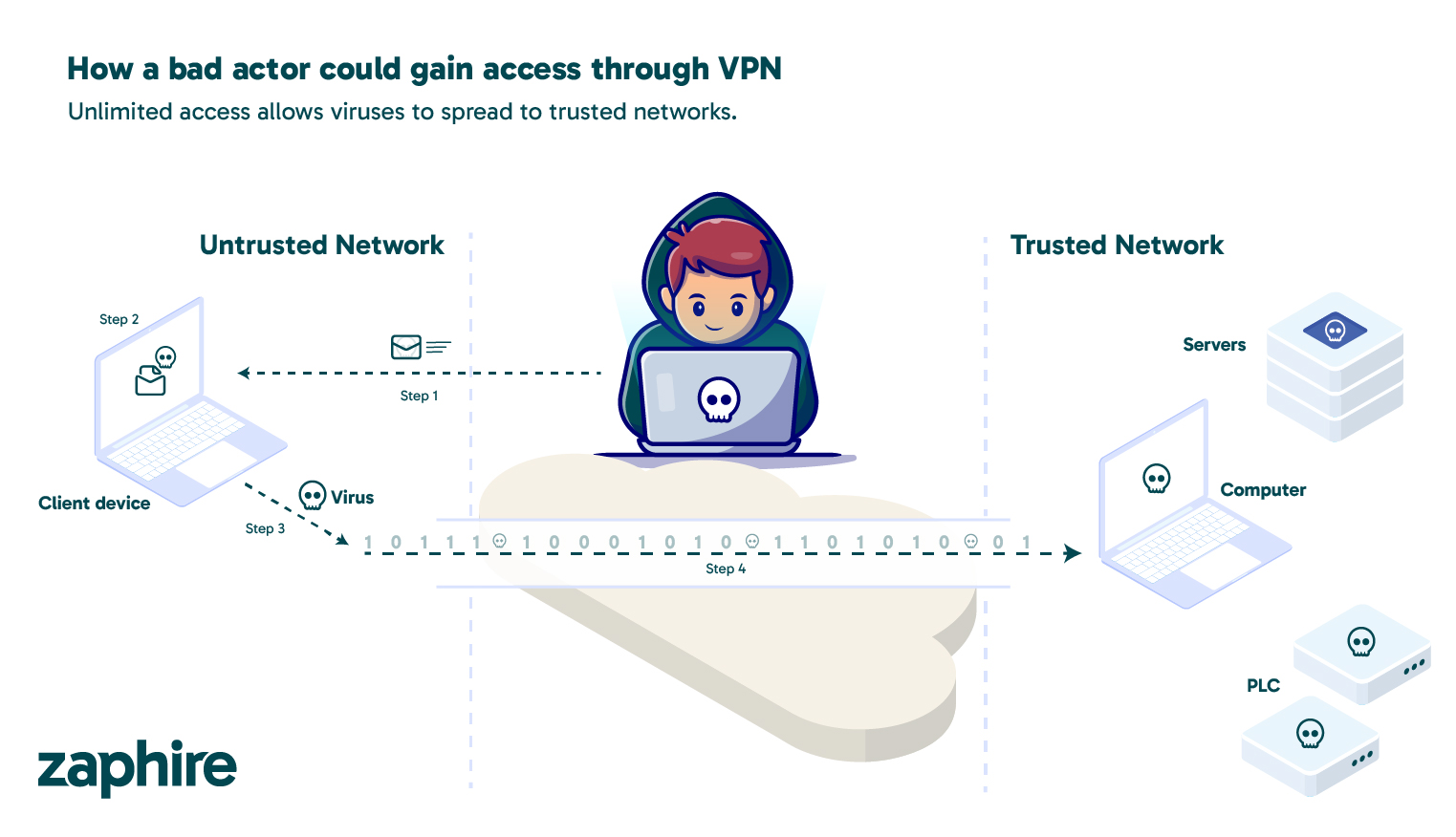
Imagine a vendor engineer receives an email with a seemingly harmless attachment, a file labeled as a project document. When opened, it silently installs a Cryptolocker ransomware payload. Because the engineer’s laptop is connected to the building network through a VPN, the ransomware immediately begins to spread through shared drives and control systems, encrypting critical files and disrupting operations.
Under Zaphire’s architecture, that same event would be contained. Our platform isolates each user session and only allows communication with specific endpoints. Even if a user’s computer were compromised, the malware would have nowhere else to go. This containment principle is at the core of our design. This approach also makes it possible to modernize and secure existing systems instead of replacing them.
Zaphire’s Security Philosophy
At Zaphire, our philosophy is simple: connectivity should never compromise security. By avoiding VPNs and adopting a zero-trust architecture, we remove the risks associated with implicit trust and network-level access.
We continuously evaluate our systems against global cybersecurity standards such as ISO 27001, NIST 800-207, IEC 62443 and the NIS2 directive. Our customers benefit from a secure, scalable platform that supports safe automation and remote management without exposing critical infrastructure.
In summary, Zaphire’s approach replaces outdated VPN technology with modern, secure, and transparent connections. We empower our customers to operate efficiently while keeping their systems protected from evolving cyber threats. Our zero-trust model ensures that every action on our platform is verified, contained, and logged, so you can have full confidence in your building’s security.